Privacy is a big issue that is present in everyone’s lives, and it naturally tends to pop into our heads, especially when we’re just browsing the internet.
It’s not surprising at all. Internet privacy is no longer just a matter of “open door in the toilet”, it is a matter of the “open door in the toilet, with someone taking our photo, selling our photos to others, and then spamming us with ads for toilet paper, sanitary napkins, and razors”. Online marketers of all kinds want to monetize our attention by tracking our browser activity and cookies, our IP address and device-specific identifiers.
In such a situation, therefore, an important question concerns many of us – how can we intelligently avoid all of this?
I have already addressed how to increase your privacy and reduce your footprint on the Internet by using browser extensions in my “The Wall Against Big Brother” article, where I explained, among other things, a bit about how cookies and browser fingerprinting work.
This time, however, we’ll go a meta-world higher. Namely, the world of the browsers themselves, which many times inhibit unwanted fingerprinting and cookies by their default settings.
And yes, after comparing and testing VPN services, we have another great comparison and testing again – this time a browser comparison.
And as was the case with VPNs, I should point out that the goal of this article is not to pick the best software to suit everyone. Personally, I don’t consider myself to be any kind of privacy and digital security expert either. Moreover, each of us has different needs and goals in privacy, let alone in other areas of our (digital) lives.
So if you expect any solution from me, you won’t find it here and feel free to close this tab. In this article, I don’t want to close things down, but rather open them up – so rather than making any verdicts on privacy, let’s just look at the privacy options in web browsers themselves, as well as other specific fictions that might be useful to you. The solution may or may not be up to you.
Little trololo intro
If we want extreme privacy, we could list XY browsers right here to start with.
Outside of terminal-based browsers like Lynx or w3m (which have no – or minimal – JavaScript support, no images, and no loading of non-HTML content), we can imagine something more “advanced”. Surf, for example, is already a graphical web browser that supports images and JavaScript, but it doesn’t have bookmarks or “classic” tabs (you navigate through tabs via Ctrl/Command + tab number in the list). Midori, on the other hand, has everything you’d expect from a modern web browser, and even includes some built-in features that replace some common extensions. Otter Browser is also an interesting project with a very nice 90t UI, but it doesn’t have any extension support yet (although it is planned).
One of the big advantages of these niche browsers is that they don’t spy on you.
But seriously now. What about everyday use?
Mozilla Firefox
I’d venture to call Firefox “the most private common browser”, but that only applies to other trackers, not to Mozilla per se.
The reality is Firefox Glean, which reports almost every browser interaction to Mozilla, containing browser session ID, unique user ID, exact timestamp, and various system information. These requests happen whenever you visit a menu (Addons, Passwords, Settings, etc.), change preferences, open a new tab, or do literally anything else. Every time you shut down the browser, Firefox sends a huge request to Mozilla that contains information about almost the entire state of the browser at the moment of shutdown.
On the other hand, Firefox has a rich set of privacy-protecting customization options outside of Mozilla. “Standard enhanced tracking prevention” blocks social media trackers, cross-site tracking cookies, and also blocks tracking in anonymous windows, cryptominers, and fingerprinting scripts. There’s also a “strict mode” that I recommend to set – while it may extinguish some sites that have trackers hidden in their content – there are also ways to enable enhanced tracking protection for trusted sites.
EFF’s Cover Your Tracks test, however, reports “strong protection against Web tracking” already in Mozilla’s default settings. Fingerprint protection currently uses a plain list of fingerprint trackers (resistFingerprinting), but Mozilla is working on an update that will make the browser look a bit more indistinguishable again.
Another option for Firefox fans is Firefox Focus, a privacy-focused browser for iOS and Android that blocks some trackers and has a custom ad blocker built in.
Mozilla also offers a VPN with the ability to connect up to five devices to more than 500 servers in more than 30 countries. Many readers may correct me when I mention that Mozilla has a built-in VPN, and say it should be called a “proxy server” and not a VPN. The difference is that a standard VPN masks your IP address from all traffic from your computer, while Mozilla’s feature applies exclusively to the browser.
Mozilla has also borrowed some Tor features to block fingerprinting, and its developers are constantly trying to improve new features.
A fantastic extension for Firefox is the Multi-Account Container, which allows users to divide their online activities into color-coded tabs that have separate isolated browsing sessions (I write more about this feature in the aforementioned article on browser extensions).
GNUIceCat
GNUIceCat is a GNU Project FOSS technology based on Firefox. The goal of GNU is to create a web browser that will not load any proprietary software, including JavaScript, digital rights management (DRM), and proprietary extensions.
An interesting add-on is JShelter, which works similarly to a traditional firewall for network connections, but instead of the network itself, it controls the APIs provided by the browser and allows users to choose which actions should be allowed, disabled, or restricted on web pages. Outside of that, it includes JavaScript Shield, which reports fake data to certain JS functions in an attempt to limit fingerprinting, at least to some extent. In many ways it resembles the classic Mozilla extension “User Agent Switcher”.
An extremely interesting and unique feature of IceCat is the TPRB (Third Party Request Blocker), which has actually many features unrelated to its name. First of all, it can block Cloudflare and it can also redirect the sites behind it to their web archive versions. However, it can also block specific CSS and JS functions, as well as downloading certain types of files.
The issue, however, is that the default settings aren’t worth much (e.g. whitelisting YouTube and Reddit, or exposing yourself to Cloudflare MitM). As for its core functionality, TPRB blocks third-party requests by default – but you can only allow them selectively by domain, not by type (so either all or none from a certain domain). Also, all third-party CSS is allowed here – which basically negates the name of this extension (although you can change it, but we’re talking about the default here).
Meanwhile, GNU IceCat has “strong protection against web tracking” according to the EFF, but in practice it remains to be a copy of Mozilla, which needs a lot of additional settings, at least if you want to achieve a bit of privacy.
Opera
Opera has a long history of innovation among web browsers. The Norwegian software company was the first to include tabs and integrated search in a web browser, and one of Opera’s developers invented CSS. Now Opera has a free built-in “VPN” (or rather proxy, as is also the case with Mozilla) and also offers a gaming browser called Opera GX. The latest version is the interesting Opera One, which adds tile-like tab management, an AI-enabled chat sidebar, and a multi-threaded compositor for faster rendering.
Opera states that it’s VPN is a “no-logging VPN”, but I don’t know what to think about that. I would venture to mention that this feature was released by Opera shortly after Opera was purchased by a Chinese investment group in 2016.
Opera also blocks ads and trackers by default, and EFF’s Cover Your Tracks reports “strong protection against Web tracking”. However, Opera understandably doesn’t have specific anti-fingerprint features, so the same test reports that Opera produces a unique fingerprint, although with the VPN/proxy feature turned on this changes to “a nearly unique fingerprint”. With its Speed Dial and handy sidebar, Opera still differentiates itself from most browsers while offering plenty of gadgets and fiddles, but it’s still more than a little far from a private browser.
Brave
Brave is a browser that emphasizes privacy and ad blocking, but also allows you to earn cryptocurrencies (specifically the shitcoin BAT) while you browse. Like most browsers today, Brave relies on a modified version of Chromium – the code that powers Google Chrome – which means it’s compatible with most websites (and is therefore also compatible with Chrome extensions and runs some Chrome features like Chromecast).
Brave has higher goals than just allowing you to hoard cryptocurrency or protecting your privacy. Its creators want to revolutionize the way online commerce works, where direct micropayments replace large-scale ads. To earn cryptocurrency rewards with Brave, the software periodically displays an unobtrusive ad in a frame outside the browser window; you can turn it off if you want.
EFF’s Cover Your Tracks states “strong protection against Web tracking.”
A feature called Shields blocks third-party cookies and ads by default here, though most trackers actually remain untouched. Brave enforces the more secure HTTPS protocol (which is common among the latest browsers) and lets you choose between Standard and Aggressive tracking and ad blocking. Brave also has advanced fingerprint protections that “randomize output from semi-identifying browser features” and disable features commonly used to reveal device information.
Brave also has other security-focused products, such as a search engine, a private messaging app, and an initiative called SugarCoat, which is designed to, in short, disable scripts that collect browsing data while preserving website functionality.
On the other hand, Brave hasn’t avoided some controversies, including its decision to whitelist Facebook URLs.
Dissenter Browser
This Brave fork was created literally in a matter of days in response to a wave of censorship from Twitter, Facebook, Mozilla, etc. Its fame lies in the fact that it is integrated with the Dissenter extension (banned in Firefox and Chrome extension stores), which allows you to comment on any article from any website, thus bypassing their censorship policies.
To use it, however, you have to sign up for their social network, which requires ReCaptcha. Then, of course, if you want to post a comment, you have to share the page you’re on with Dissenter, which – if used extensively – can create a pretty decent profile of your browsing history.
The browser itself includes the usual Brave features such as Shields, whitelisted trackers and safebrowsing. Overall, this browser is just a fad that rides the anti-censorship wave. If we could be a bit more cynical, we could call it a honeypot designed to collect browsing history and comments from as many people as possible and share them with a large centralizer (Cloudflare).
DuckDuckGo
This well-known search engine already has its own browser, but at the time of writing it is still in beta.
This Chrome-based innovation has a few design tweaks. For example, the flame button at the top (it works a bit like a privacy panic button) lets you close all tabs and clear all browsing data.
The UI is surprisingly nice, the search bar is centered, each new tab offers custom site buttons and a list of previously visited pages with the number of found and blocked trackers for each.
The browser also includes automatic cookie consent management for pop ups and supports the emerging Global Privacy Control standard.
Another advantage is the Duck Player for playing videos without Google ads, which works surprisingly well.
If you want to make your privacy even more robust, you can also install the DuckDuckGo Privacy Essentials extension to your browser. It will block third-party trackers, force sites to use HTTPS (which virtually every modern browser already does), and allow you to view a privacy score for the sites you visit.
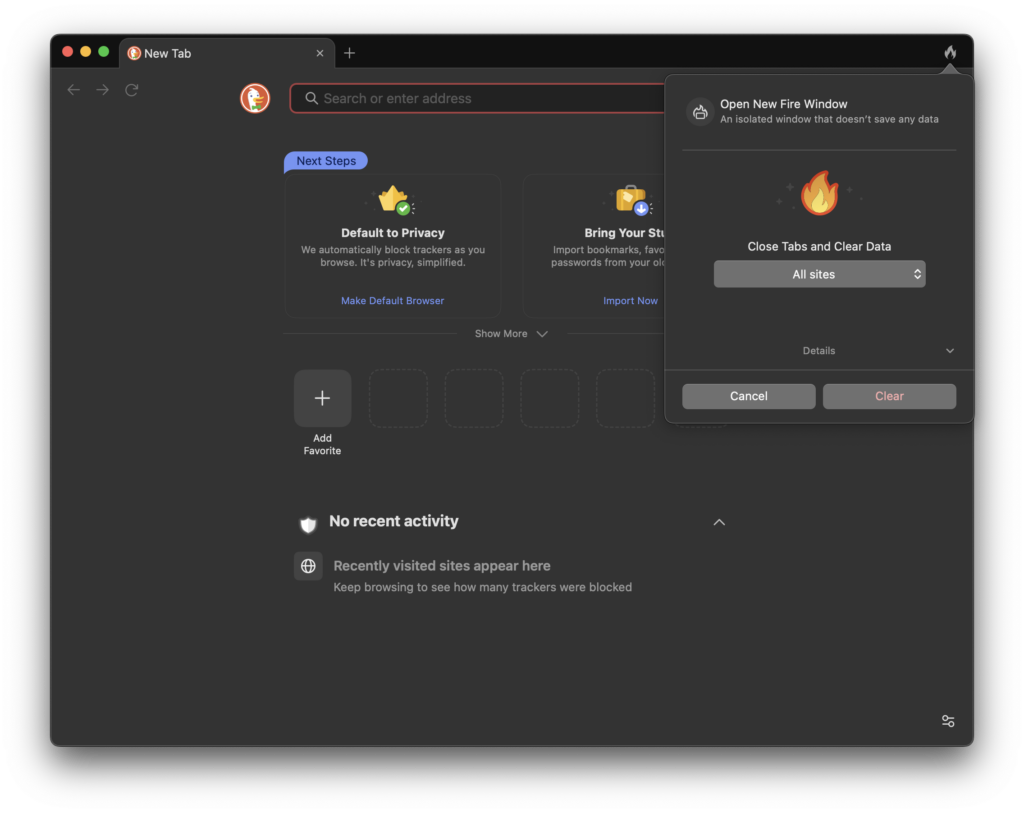
Epic Privacy Browser
Like Firefox and Opera, Epic Privacy Browser has a built-in VPN-like feature with its encrypted proxy server that hides your IP address from the web.
The company claims that Epic blocks ads, trackers, cryptomining, and even ultrasound signaling. It also blocks fingerprinting scripts and prevents WebRTC, among other things.
EFF’s Cover Your Tracks, however, reports only partial protection from ads and invisible trackers with Epic’s default settings for this browser. Thus, the same score that Google Chrome got, which really isn’t much.
However, when you press the umbrella button in the browser which launches the local built-in version of uBlock, EFF already throws up “strong protection” against web tracking.
The browser UI looks almost identical to Chrome/Brave except for a few privacy and proxy settings.
Ghostery
The Ghostery browser is based on Firefox modified to include the Ghostery extension. By default, it also uses its own Ghostery private search page, which interestingly displays a number of tracking and ads of the resulting links. The company offers the Ghostery Privacy Suite and maintains a database of trackers at whotracks.me.
In my case, Ghostery works even faster than Firefox itself, and its nice minimalist design is a big advantage. However, it didn’t do as well as Firefox in EFF’s Cover Your Tracks test, as it was given “some protection against Web tracking, but it has some gaps”. So in reality, this is a worse result than Firefox itself with the default settings, and a similar result to what we can achieve with Edge and Safari.
Moreover, the Ghostery extension itself was legally accused of selling data to advertising companies in 2013. While that’s a decent history, make up your own mind.
LibreWolf
LibreWolf is yet another Firefox imitator that strengthens security and removes any hint of the “phoning home” that many browsers from big corporations like Apple, Google and Microsoft contain.
LibreWolf certainly won’t win any awards for UI as it doesn’t offer any additional features with its minimalist interface outside of tabs, bookmarks and history (but it doesn’t even pretend that this should be its intention). For me personally, however, I find it hard to use.
It comes with the uBlock anti-tracking extension installed, uses DuckDuckGo as its default search engine, and is credited in EFF scores with “strong protection against Web tracking.” The browser is so focused on not sending data to servers that it disables Google Safe Browsing protection, which is enabled in standard Firefox, for example.
TempestBrowser
Tempest is a relatively new browser based on Chromium, which comes from the search engine of the same name (the homepage is therefore understandably set to Tempest search). It’s practically Chrome with a few privacy features.
You can also add side buttons in the browser, but unfortunately you can’t change the start page. Very cool thing is that Tempest offers encryption of search terms and display of privacy reports for searched sites. In Settings, you have a choice of three privacy levels: No Blocking, Block Trackers (the default setting), and Block Ads and Trackers. That’s certainly more than Chrome.
By default, the browser uses Cloudflare’s DNS server, which is certainly preferable to the server provided by your ISP. The security settings only offer the option of Standard Protection or none; the classic Chrome Enhance Protection is not available, probably because this protection sends data to Google.
In EFF’s Cover Your Tracks, this browser was the only one besides Brave to report a randomized fingerprint. However, it received only partial credit for its protection from ads and trackers, even after checking the “Block Adds and trackers” feature in Settings.
It would also be kind of dumb not to mention that the software’s founder Michael Levit has a history of selling previous services to Chinese companies, but on the other hand, he himself took the so-called “Founders’ Pledge” and pledged to donate half of Tempest’s proceeds to fight climate change.
So come on, screw privacy – let’s all download TikTok and Tempest and take a selfie with Greta!
Vivaldi
Vivaldi, a private fork of Opera that also uses Chromium code, is probably the most customizable browser on the market. It includes innovative features such as built-in translation, split-window view, tab groups, notes, link sidebar and mouse gesture support. It also now includes workspaces, which allow you to group related browsing sessions together as well. This built-in feature is reminiscent of Firefox’s Multi-Account Containers extension.
Vivaldi includes built-in ad blocking and trackers, although it doesn’t specifically try to prevent the use of fingerprints. Like virtually all other browser features, the privacy settings here are both very deep and detailed. The EFF scores Vivaldi a “strong protection against Web tracking” with tracking protection turned on, although a unique fingerprint was still registered.
Waterfox
Waterfox is another Mozilla. The organisation behind Waterfox has recently separated from its corporate owner, so it is now an open-source project. The browser’s documentation includes a clear privacy policy and uses the same Enhanced Tracking Protection as Firefox. The browser’s page states that “unless you explicitly sign up for a web service with us, we don’t want your personal information, and we don’t touch it”. The tracking protection in Waterfox is thus identical to that in Firefox, which claims to protect against social network trackers, cross-site tracking cookies, fingerprinters, cryptominers, and trackers hidden in ads, videos, and other content. You can turn off WebRTC here for added privacy.
Like Firefox, Waterfox allows you to sync bookmarks, history, tabs, passwords, add-ons, and settings. The browser uses Oblivious DNS technology, which hides your web requests from your provider. You can also use all the extensions and themes designed for Firefox. EFF’s Cover Your Tracks lists “some protection against tracking” as Waterfox’s default setting, but switching to Strict yielded a “strong protection” result in the test. With both settings, however, EFF reports a unique fingerprint, despite Waterfox’s claim of fingerprinting protection, which, like most browsers listed here, uses only a plain block list rather than randomly selecting fingerprint data as Brave does.
PaleMoon
Palemoon is another Firefox-based browser, but it borrows a few key features from Chrome UI (many Mozilla extensions don’t work on it). The default search engine here is DuckDuckGo.
PaleMoon is pretty oldschool by the standards of all “mainstream” browsers. It supports GTK2, XUL add-ons, is not tied to big corporations (like many mainstream browsers), and deliberately disables some “modern” stuff.
On the other hand, Pale Moon now has WebAssembly enabled by default, which basically turns your web browser into another operating system; because it’s literally an assembler into which you can compile other languages and run all sorts of “applications”. Of course, something like this brings with it a host of new security vulnerabilities.
So we can understandably find very conflicting opinions about PaleMoon all over the Internet, but among the most common of them is just that it was once a relatively good, albeit conservative privacy-focused browser that has degraded over time into a kind of weird and broken experiment.
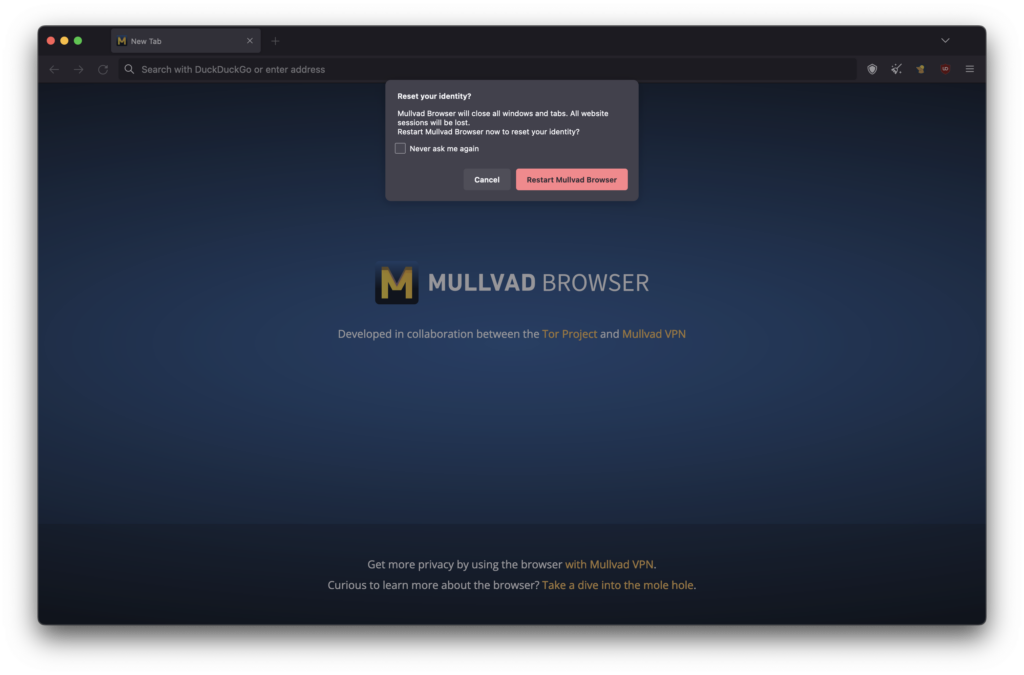
Mullvad
Mullvad Browser is another browser that is built on the open-source code base of Mozilla Firefox. The browser is a collaboration between the Mullvad VPN service and the Tor project, and its UI looks virtually identical to Tor’s, except that it doesn’t offer true Tor functionality (unlike Brave).
In a leak test, Mullvad’s browser outperformed most other browsers in that it did not experience any DNS or WebRTC leaks. Another interesting feature is “Reset your identity”, which effectively resets the browsing session and clears cookies and history (so it works virtually the same as the Flame Button on the DuckDuckGo browser).
The browser ships by default with the uBlock Origin extension. The default search engine here is DuckDuckGo.
The Mullvad browser does push you to register MullvadVPN, which can be a disadvantage if you don’t have it. However, the browser doesn’t seem to have very strong fingerprint protection, exhibiting a unique fingerprint according to EFF’s Cover Your Tracks test.
Tor Browser
The slogan of the Tor browser (short for the onion router) is “Protect yourself against tracking, surveillance, and censorship.” This is the highest possible browser privacy protection, and the EFF test therefore understandably states “strong protection against Web tracking.”
It provides a multi-stage encrypted route for your browsing that makes it much harder to identify you. It provides even more privacy than a VPN alone, as your encrypted traffic passes through at least three nodes. The first node knows the source but not the destination of the traffic, the middle nodes know neither, and the last node knows only the destination. This system makes it nearly impossible to trace the traffic back to you. The downside? It slows down your browsing quite significantly.
If you set Tor to the most secure level of protection and disable JavaScript, many common sites understandably won’t run – basically any that contain interactive content, like YouTube. In addition to providing privacy and access to the standard web, Tor also gives you access to sites that use a custom onion protocol that is separate from the standard web, often called the dark web. EFF’s Cover Your Tracks states “strong protection against Web tracking”, but also “your browser has a unique fingerprint”. However, changing your browser’s privacy settings to Safest leads to top-notch fingerprint protection. Still, you can’t do much on the web with this setting because it disables JavaScript.
In addition, Tor Browser implements various strategies, such as warning users when the browser window is maximized, introducing default fallback fonts to prevent canvas fingerprinting (I write more about this in my article on cookies), and setting specific resolutions for JS clock sources and for timestamps (to prevent time-based fingerprints).
An even more private way to run Tor is via Tails, a portable Ubuntu-based operating system that you run from a USB drive. Tails doesn’t store any unencrypted data from your browsing session and leaves no traces on your computer’s disk.
Conclusion
We’ve compared the different browsers and extensions to see how they vary and which is best for different use cases.
Choosing the right browser is up to you, but it’s worth mentioning that any private browser should at least limit web tracking, clear your browsing history and cookies. Of course, all of the above also depends on your settings.
If you want to experiment for yourself with choosing the right browser and with its settings in order to achieve optimal functionality and privacy, I recommend you test it directly on EFF’s Cover Your Tracks website. EFF uses a real tracking company for its tests, but doesn’t provide its name.
Other tools you can use to find out your digital fingerprint include AmIUnique and Device Info.
